E-Commerce
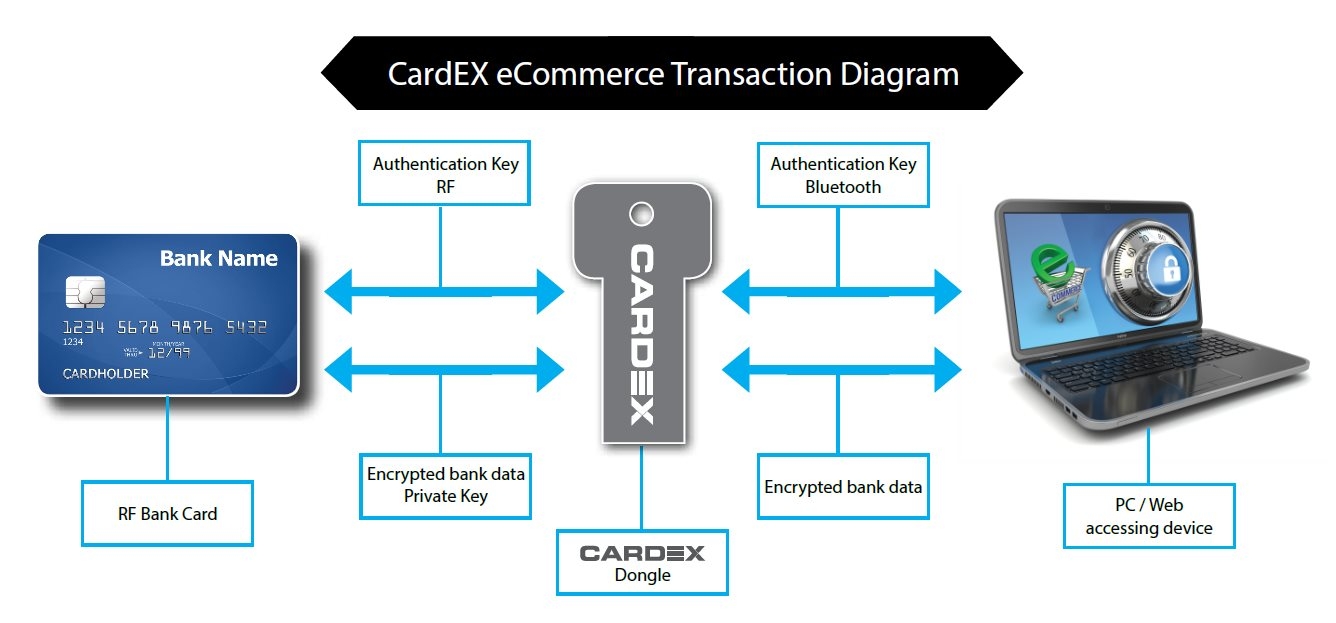
The IDAT sphere of technology extends to E-Commerce. IDAT's core feature is that it ensures "card-present" E-Commerce transactions. The vendor is supplied with an IDAT payment API that will connect with its payment portal and filter back to the card issuer for authorisation. This is achieved with a flash disk sized dongle that provides authenticated communication between the customers RF enabled bank card and their web accessing device i.e. a tablet, smart phone, laptop or desk top.
The dongle is supplied by the card issuer as a pair to the RF enabled bank card. IDAT custom design and manufacture these dongles. The software inserted on these dongles is the intellectual property of IDAT, which is also protected with IDAT's DataEX technology, making it both uncloneable and unhackable.
The underlying principle behind this methodology is that the dongle acts as a virtual ATM/POS between the card and the web accessing device, initiating the E-Commerce transaction. The same encrypted cocoon of data that is sent via an ATM/POS is sent via the dongle to the web device and passed to the payment portal. This includes device authentication.
The vendor API requests a cocoon of payment data from the dongle. This is preceded by authentication between the dongle and the API using a dynamic SHA3 hash (token) of the card issuer's authentication key.
Once the web device and the dongle have authenticated, the dongle authenticates with the RF enabled bank card again using a new dynamic SHA3 hash (token). These authentications are bilateral and simulate a card to ATM/POS authentication.
The RF enabled card communicates with the dongle via encrypted RF after which the dongle communicates with the web device via high speed Bluetooth. The reason for the latter is to include Apple products that have web access but are not equipped with USB ports as an example.
Once the encrypted cocoon of data is received by the web device, this is sent via the API to the payment portal of the vendor. No bank card number or CVV2 manual input is required and eliminates the threat of replication or interception. The cocoon of data acts like a token and will only be valid for a predetermined time period (default is 5 minutes) and for a single transaction. It is important to note that the encryption key (PK) is entirely different to the authentication key (CI).